Search
Identity lifecycle
In any ID system, the process of establishing a person’s identity and then using this identity in later transactions involves multiple stages often referred to as the “identity lifecycle”. This lifecycle is vital to creating trust in a variety of transactions between people, identity providers, and public and private sector relying parties.
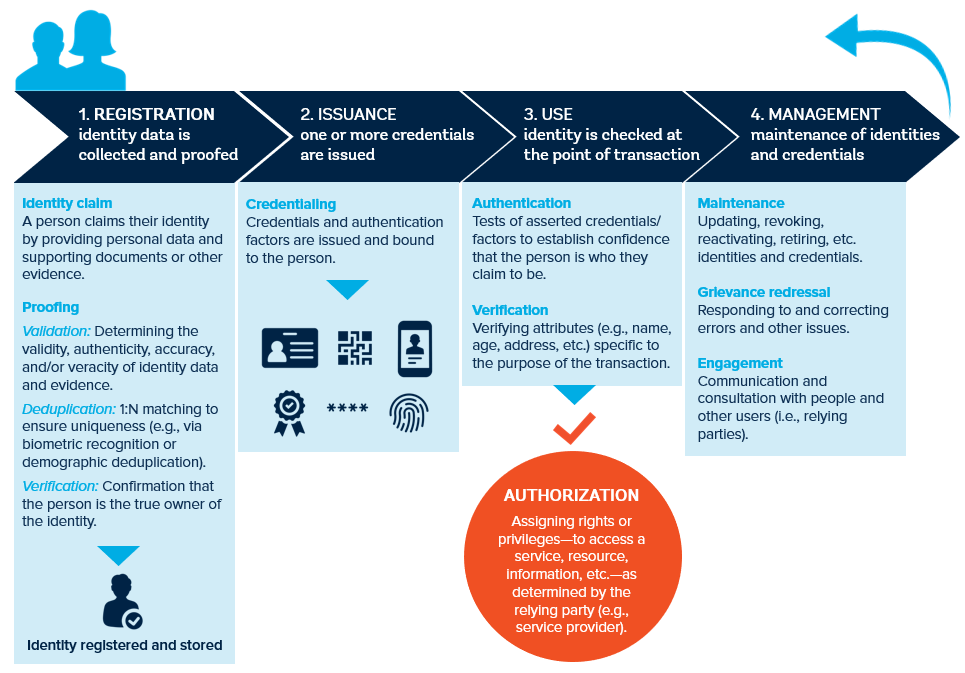
As the name implies, the identity lifecycle is not a one-time event (see Figure 6 below). Rather, it is a process that starts when a person first registers and their identity is created; continues with authentication of that identity and updates to their attributes and credentials over time; and ends when an identity record is retired or invalidated (e.g., after death, request for removal by the individual, or some other event). As discussed above—and in the section below on stakeholders and roles—the lifecycle may be completed by a single actor (e.g., an ID authority) for a given ID system, or may be split between multiple public and/or private sector actors (e.g., different registration authorities vs. credential and authentication providers).
Figure 6. Identity lifecycle
Source: Adapted from Digital Identity: Public and Private Sector Cooperation and Technology Landscape for Digital Identification
The technology and protocols used throughout the lifecycle—including for registration, credential issuance, authentication, and management—are critical for ensuring the inclusivity and trustworthiness of the system and its ability to facilitate authentication for different transactions at the appropriate “level of assurance.” Each stage is described briefly below.
Registration
The lifecycle begins when an individual first registers their identity, which involves two main processes:
- Identity claim. Registration begins with capturing and recording attributes from a person who “claims” a certain identity, such as biographic data (e.g., name, date of birth, gender, address, email) and biometric features (e.g., fingerprints, face, iris scan). It also may include the collection of meta-data about the time and location, location, and other details of the claim, which might be necessary for auditing purposes. During this process, people also typically provide supporting documentation or evidence to substantiate their claimed identity or—in the absence of such evidence—they may have their data vouched for by a trusted person, such as a local government official. Which attributes and evidence are captured during this phase, the methods and standards used to capture them, and the resulting data quality will have important implications for the inclusivity and trustworthiness of the identity, the speed of data collection, program cost, interoperability with other ID systems, and its utility for various stakeholders.
- Identity proofing. Once a person has claimed an identity, the data they provide is then validated. This involves checking the validity, authenticity, and accuracy of the supporting documents or evidence provided and confirming that the identity data is valid, current, and related to a real-life person. Identity proofing also commonly involves a deduplication process to ensure uniqueness based on biographic data and/or biometric recognition (e.g., in cases where there is no trusted source of identity information). In some cases, identity proofing also includes a process to verify that the applicant is the true owner of the claimed identity and evidence (e.g., through biometric verification or a visual comparison of the physical person to a photo on a previously issued ID card).
Issuance
After registration, the identity provider issues one or more credentials and/or authenticators—e.g., cards, certificates, PINs, etc.—that can be used by a person alone or in combination to prove or “assert” the identity that has just been created. For an ID to be considered digital, the credentials issued must store data electronically and/or be usable in a digital environment (e.g., being machine readable and/or usable on the internet). As with registration, the types of credentials issued, including their form factor and security features, have important implications for the robustness of the system to identity theft and fraud, as well as accessibility. In addition, the format of credentials such as cards is a major driver of the cost of ID systems.
Authentication
Once a person has been registered and credentialed, they can then authenticate or “prove” their identity when needed to access associated benefits and services. The authentication process can involve one or multiple factors—i.e., identity credentials and/or attributes. For example, people may use a username and PIN to login to an e-government portal to pay their taxes or use their card and photo or fingerprint to prove their identity at a hospital.
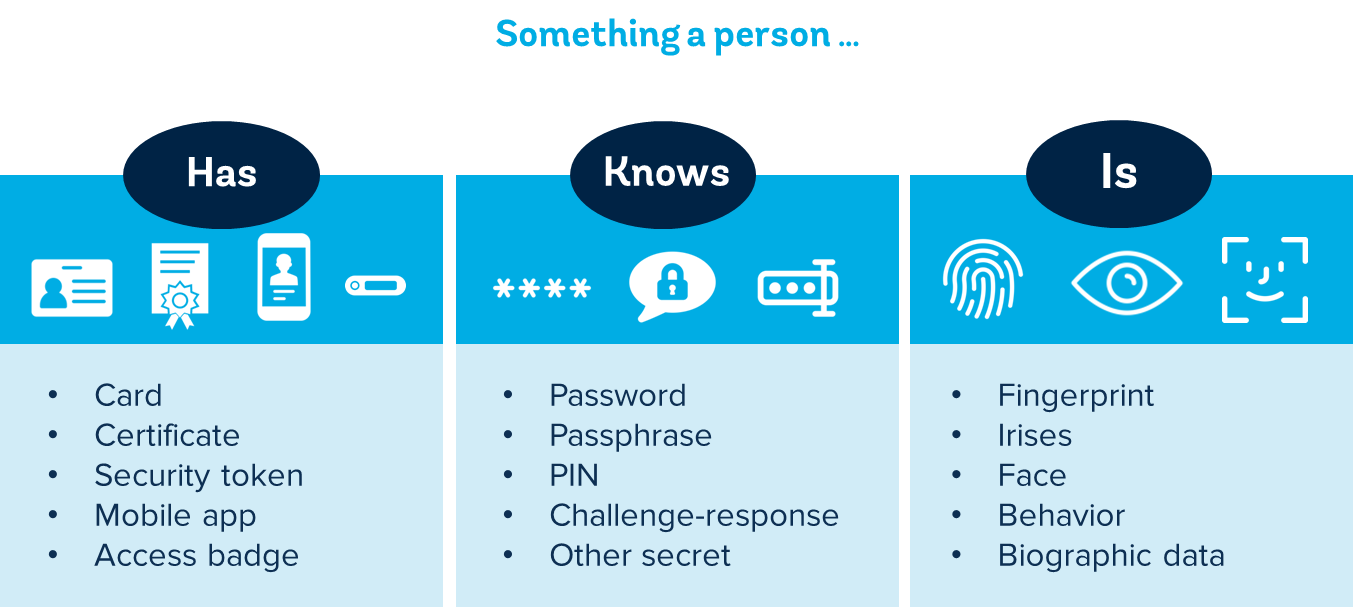
Authentication factors fall into one of three categories (see Figure 7), including: (1) something you have (e.g., a physical card, mobile device, or digital cryptographic key), (2) something you know (e.g., a password, PIN, or answer to a secret question), or (3) something you are (e.g., your fingerprint or other biometry). Using multiple factors increases the level of assurance (i.e., security or trustworthiness) in a transaction.
Figure 7. Common authentication factors
Source: Adapted from Digital Identity: Public and Private Sector Cooperation
In addition to, or as part of the authentication processes, ID systems can also be used to verify specific attributes of a person—e.g., their name or age—in accordance with regulations on data sharing. This can be done using the credentials that a person presents (e.g., info stored on a card’s chip or a barcode), and/or by querying the database directly.
Authorization
Once a person has been authenticated, the relying party (e.g., a service provider) may undertake a separate (but sometimes automatic) process to determine whether a person is authorized to access different services or transactions or perform some certain actions. For example, successful authentication may allow a person to prove their identity when attempting to enroll for a government benefit, but the decision to authorize them to receive a particular cash transfer or type of pension may require the verification of additional information (e.g., their income or occupation).
Management
Throughout the lifecycle, identity providers manage identity data and credentials through a dynamic process. Importantly, this includes updating and re-proofing identity attributes that change over time—e.g., address, marital status, profession, facial image, etc.—as well as updating, renewing, revoking, or deactivating credentials. These updates can be subject to proofing (compared with accepting self-declared information), but strict requirements can act as a disincentive for people to keep their data up to date or may even exclude them from being able to update data (e.g. requiring proof of an address). Identity records may be retired if it is discovered that they were fraudulently created, after security breaches, or following an individual’s death. Identity providers must also work to correct errors, address grievances, and continuously engage with the public and relying parties.
